A VERA Files colleague (Let’s call her “A.”), who is based in Mindanao, received a call last week from a number not listed in her contact list, asking if she knew a certain person, who happened to be another colleague (“B”) in VERA Files.
She replied “Yes” and inquired why she was asking. The caller said she was actually contacting “B” because he took a loan from their company and had listed her (“A”) as a reference person.
“A” told the caller that she is not based in Manila. The caller asked “A” to pass the message to “B” to settle his loan. “A” sensed something fishy so she immediately blocked the number and the SMS that came later.
“A” then asked “B” if he had made her as a reference for a loan and the latter said he did not.
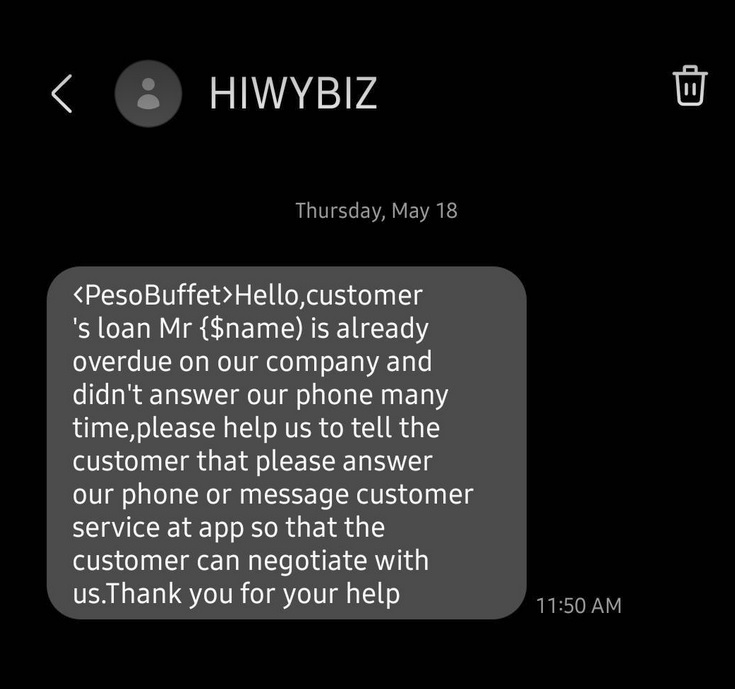
On that same day, another colleague (“C”) received a call from a certain “Joana” of PesoBuffet, a lending company known for its high interest rates, asking if he knew a person named Raymond (“C” couldn’t recall the surname.). She said they couldn’t contact him and the name of “C” was one of those listed by Raymond to call if he is not available.
“C” said the caller was polite and even apologized for bothering him with the inquiry.
“C” does not exactly consider it a scam but he was still alarmed because someone used his phone number.
“Either some malicious app managed to access my mobile device or someone got it from the countless contact tracing forms that I have filled up,” he said.
We learned later that the phone of “B” was hacked and those scam agents must have gotten their numbers from there.
“A,” who is our tech gal, said one way that our numbers are accessed by scammers is through the apps that we install in our smartphone.
She said: “When we install apps in our smartphone, it usually asks permission to access our phone’s contacts, media, storage and what not. Usually, you don’t really have a choice because you can’t install the app if you don’t give permission to those items, so just be cautious.
“If the app is asking for permissions not significant to the apps’ function, then don’t give permission. If it’s necessary, just give permission while the app is being used. If the app is not so important better not install.
“If you’re installing a game and it asks access to your contacts– then it’s quite suspicious– better not install the game.
“Be discriminating. Only install apps from your smartphone’s app installer and not from a link of a promotion/ad you saw in your social media feed. Only install apps developed by reputable or legitimate institutions. When you search for the app to install– look at who developed the app, the logo and a badge that it’s recommended or editor’s pick — to check if they’re legitimate.”
“A” suggests installing an antivirus. Upon her recommendation, I installed Bitdefender Mobile Security free version on my phone.
She said: “An antivirus installed on your smartphone is a layer of security, but still your personal practice– how you use your smartphone– is the one that matters and the one that will give you security and protection.”
Another target of scammers are bank accounts and credit cards. I have received calls purportedly offering to assist me in updating my bank accounts. I just dismiss them as scammers or reply to them that they should stop their illegal operation.
Security Bank gives these tips to its clients:
• Be skeptical when you receive messages from any sender. Security Bank will never ask for your OTP, CVV, and PIN via call, text or email.
• Ask questions and probe further. Fraudsters are trained to sound very convincing. Don’t be afraid to ask questions to verify the legitimacy of a call.
• Scrutinize emails and text messages received. It helps to pay close attention to messages you receive. Check for grammar or spacing errors.
BDO has almost the same advice:
• Do not share username, password, OTP and card details (card number, expiry date and CVV.)
• Do not click links. BDO will not send links via email, SMS and Viber.
• Do not reply to suspicious senders. Visit the BDO website and search for “BDOStopScam” to view all official BDO sender names.
Stay vigilant.
This column was carried also by VERA Files and Malaya Business Insight.
Be First to Comment